European Directive
- European legislation on eSignature
- UK notifications under article 11 of the electronic signatures directive
Accessibility
Frequently Asked Questions
Welcome to tScheme Frequently Asked Questions page.
Below we have tried to answer many of the most common questions asked of us. Some of the information is available on other sections of the site and in these cases, you are redirected there. The list is of course not definitive, and tScheme is always willing to provide information and answer questions.
We have tried to address both questions relating to tScheme structure and operation, as well as a brief technical description of the system of Digital Signatures and PKI.
Please email us if after looking through this page you still are in need of an answer.
What is tScheme?
What does tScheme Approval mean?
What services have tScheme approval?
What is a "tScheme Registered Applicant"?
What is a "Qualified Certificate"?
Why get tScheme Approval? (or Why look for tScheme Approved Services?)
How does the system of secure e-communication work?
What is a Digital Signature?
Who can I trust to provide me with good security?
- What is tScheme?
tScheme is the industry-led, self-regulatory, not-for-profit organisation set up to create strict service criteria and to approve electronic trust services, including qualified certificate services. tScheme approval will provide assurance to individuals and companies relying upon electronic transactions, enabling growth in e-business.
tScheme develops sets of criteria called Approval Profiles for commercially offered trust services. These allow service providers who are able to demonstrate that their services meet these sets of criteria to achieve added business value by using the tScheme approval mark. A contract is put in place to safeguard continuing good practice.
To obtain this necessary proof of trustworthiness, a trust service provider is assessed to the relevant profiles by an independent tScheme-recognised assessing body. A report is prepared, and if this certifies compliance with the tScheme criteria, the trust service is granted approval by tScheme Ltd, including the right to display the tScheme mark.
Membership of tScheme is open to all sectors of industry, and to trust service users, ensuring that tScheme continues to address true market priorities.
For a more detailed answer, we have a brief in our About section
Back to Top
- What does tScheme Approval mean?
tScheme defines standards of good practice for electronic trust services, evaluates individual electronic trust services against these standards, and awards approval to those which meet the standards.
The Trust Service Providers offering the services must also have been assessed against the tScheme Base Approval Profile. All assessments are carried out by tScheme-recognised assessors. The tScheme Profiles have been written by expert groups, and are compatible with both the ETSSI standards, the Electronic Communications Act 2000 and the European Electronic Signatures Directive (1999/93/EC - or simply "the eSignatures Directive").
Back to Top
- What services have tScheme approval?
For a current list of approved tScheme Services please take a look at the Directory of Approved Services. Here you will also find a list of our Registered Applicants.
Back to Top
- What is a "tScheme Registered Applicant?
As an initial step toward gaining tScheme Approval, Trust Service Providers may apply to tScheme for Registered Applicant status. This in no way implies any form of tScheme approval, but recognises the firm commitment the service provider is making to complete the tScheme assessment process in a timely manner. After submitting a letter of application, naming the service(s) to be considered, a timetable for achieving full Approved Status (within a 12 month period) and a draft Specification of Service Subject to Assessment (S3A), the request is considered by the tScheme Secretariat that then makes a recommendation to the Approvals Committee to be considered at the next scheduled meeting. A list of current Registered Applicants is here.
Back to Top
- What is a "Qualified Certificate"?
A Qualified Certificate is defined by the eSignatures Directive (1999/93/EC and transposed into UK law by the Electronic Signatures Regulations 2002), but is essentially a certificate containing certain information and provided by a competent service provider who has verified, by appropriate means in accordance with national law, the identity of the subject of the certificate.
When it is the basis of an Advanced Electronic Signature (defined in the same sources) and when the signature is created by a secure-signature-creation device, then it is usually referred to as a "Qualified Electronic Signature" and must be treated the same as if it was a hand-written signature. NB. not all tScheme Approved Services will necessarily provide Qualified Certificates, although many will because of the potential legal benefits.
Back to Top
- Why get tScheme Approval? (or Why look for tScheme Approved Services?)
An independent, self-regulatory, scheme such as tScheme provides benefits to each party involved in the e-business equation. tScheme has created a unique framework for commercial trust services approval, which is totally responsive to emerging e-business markets. tScheme handles all the complex issues and has managed and arranged all the research and assessment so the relying party does not have to know anything about the trust service they choose, save how to use it, that it meets their needs, and that it has been tScheme approved.
Business and consumer confidence is vital, especially in an emerging high technology sector such as digital signatures. An independent, transparent body can provide the assurance needed to place trust in both the service providers and their services. A body such as tScheme specifically takes into account all the relevant legislation and has access to top experts who define the criteria, to which services are assessed.
The tScheme mark, the Approved Service mark, and the Registered Applicant Sign, are all registered trade marks, and use of it can only granted by tScheme. Whilst tScheme’s approval profiles are available openly, they are also copyrighted documents, and have a controlled distribution.
tScheme adds value to a service by assuring the user that it has independent approval. A TSP might be able to assess its own electronic trust services using tScheme’s approval profiles. However, there is little to be gained from this without then completing the process of tScheme approval. Services with the tScheme Mark will be known by those in the industry, and the general public, to have been assessed to an extremely high, independent, standard.
Also, under Article 7.1(a) of the eSignatures Directive, all EU Member States must ensure that certificates issued by providers of Qualified Certificates to the public that meet the requirements of the Directive and are ‘accreditted’ by tScheme are recognised as legally equivalent to Qualified Certificates issued by a TSP established within the European Community.
Back to Top
- How does the system of secure electronic commerce work?
In summary:
- A Registration Authority (RA) verifies the identity of an individual. Then a Certification Authority (CA), using Public Key Infrastructure Technology provides the user with two keys.
- The Private Key is held securely by the user.
- The Public Key is held by the Certification Authority and is available to all.
- Only the Private Key can be used to create a digest (hash) of the message that can then be verified by using the Public Key, this is called ‘Signing’.
- Only the Private Key can "unlock" a message locked (encrypted) with the Public key.
- Using both your Private Key and another’s Public Key you can send them a secure/confidential message, that can be proved to originate from you.
Secure e-Commerce centres around a system called Public Key Infrastructure (PKI). The Infrastructure is used to control and manage the three main elements: two keys (a Public Key and a Private Key) and a Digital Certificate. These keys, whilst not being identical, have a mathematical "relationship". The public key is usually held by the Trust Service Provider, and is available to anyone. The private key is held securely by the individual or company that it ‘belongs’ to. The Digital Certificate is issued by a Trusted third party; information on this is detailed in the next question.
The two main security functions of the PKI, are sending encrypted information (emails and attachments) and sending information that cannot be repudiated. It can be guaranteed to be from you and has not been altered by a third party. These functions can also be combined.Keys are at the heart of the PKI, although in fact, the term ‘key’ is somewhat misleading, because the encryption, which is done using a complex algorithm, is ‘one way’. Whereas a physical key can lock and unlock the same door, only the private key can decipher a document "locked" (encrypted) with the public key. It is vital to understand that the algorithm is designed so that a document encrypted with the public key can only be decrypted with the private key. Otherwise the system would be flawed; fundamentally, not even the public key will decrypt it. Similarly, a digest of a message created by the private key can only have been created with that Private key; the Public key will of course confirm this.
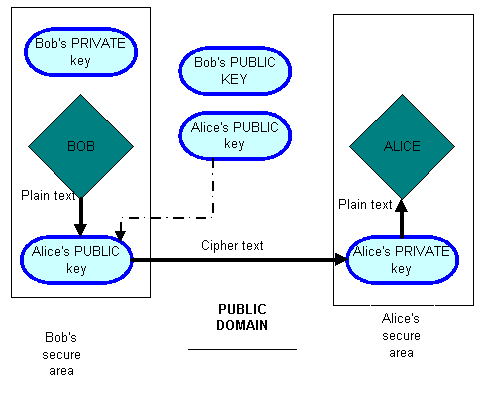
Bob writes his plain text message and whilst still within his secure area (for example, his home computer), encrypts it using Alice’s public key.
Alice’s public key is available in the public domain (i.e. anyone can use it), although Bob can use it within his secure area. Once the message is "cipher text", or encrypted, it can be openly transmitted through the Public Domain to Alice.
Alice would then use her Private Key, held only in her secure area, to decrypt the message into plain text, and thus read it. The diagram above illustrates this. The physical equivalent of secure document PKI would be a series of empty rooms, each with a locking door, that is left open, and each has the name of the room’s owner above the door. To pass on private documents to someone, you merely locate one of their rooms, and go inside and leave the documents there. When you leave the room, you close the door behind you, and this locks the door. With the room locked, only the room’s owner/key holder, with their private key, can gain admittance to the room.
The other function, which is equally important, is that of ensuring the document is from a specific individual. This is called digitally signing a document.If Bob wants to send Alice an email that she knows is from him, he needs to send her a "signed" email. By using his Private key he can create a ’hash‘ function of the actual message - this is rather like a summary. By doing this, he "Digitally Signs" it. Using his Private key makes this summary unique. The summary (hash function or now technically the signature) and the message are transmitted in plain text to Alice. Alice can then use Bob’s public key to confirm that the summary was created using Bob’s Private Key, and that the document has not been changed.
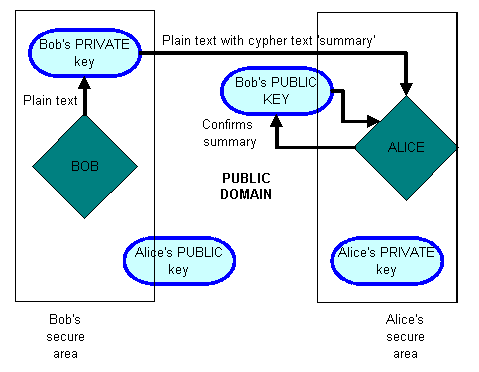
The two keys are designed for use in an algorithm, meaning that only the Private Key can decrypt a message encrypted with the public key. Likewise, only the Private Key can "sign" (hash function) messages.
The owner of the document uses a complex algorithm to produce a digest or hash of the document, such that any change to the document would produce a different result. This hash value is then encrypted using their private key. Anyone can then use the matching public key to recover the original hash. If they repeat the algorithm on the document they have received, they can compare the resultant hash with the original hash. Providing the two values are the same they have verified the sender as being the owner of the private key and that the document has not been altered in any way.
Returning to our physical equivalent, here we are using a separate group of pre-locked rooms each with one big window. Only the private key owner can open the door and place the information inside. Anyone is able to access the information (the digest) by reading it through the window, but because it is in the room, you can be sure only the Private Key holder put it there. If the observer also produces the digest for the message then, provided it matches the digest in the room, not only has the message come from a specific person, but it has not be altered in anyway. Of course, with email and the Internet, we have to think of these rooms as being "virtual", and mobile.
Another way of looking at a digitally signed message would be like sending a message contained inside a briefcase with a padlock on it. The key to the padlock is readily available to anyone - the privacy of the message is not at stake here - but the padlock is something that only the message originator (the Private key holder) could have locked. Therefore, if the corresponding public key opens the padlock, then you can be certain that the message came from the person who has control of the padlocks.This system can be described as "asymmetric encryption", because the keys are not the same and have different privileges. In a "symmetric" system, both parties would have an identical key. Despite the fact that the actual encryption process is much more efficient and quicker, the problem with this latter system is that both parties must have previously exchanged keys. Returning to the analogy, the parties would have to physically meet to exchange keys. The more people who had a key to the room, the more likely someone is to lose the key.
However, by combining the two methods, a very efficient, secure communication path can be established. The asymmetric system is used to negotiate securely a pair of symmetric keys. These keys can then be used to manage a much more efficient, secure conversation. This is essentially the process behind SSL security for secure Internet access.
Public Key Infrastructure has another major advantage. That is that it can be used for a variety of quite different purposes. You can send confidential messages, yet also send messages with proof of identity. PKI can also be used to authenticate web sites - whenever you see the padlock symbol in your browser showing as locked (and, on newer systems, with the address bar shown in green or highlighted in some other way - according to the make of browser being used), the chances are some sort of keys and certificates are being used to determine the origin of the information - vital in the days where anyone can buy/operate a .com or a .co.uk website.
The above description is an attempt to put a highly complex system into an explanation that can be understood by those with no prior knowledge of PKI. Whether it succeed is a individual, case-by-case matter for each reader. However, it does demonstrate the complexities of the system. Trust Service Providers typically try to minimise the amount of understanding a user needs to use their signatures. On the whole they are very successful. Yet this leaves you in the position that your system is rather like a magic box. You assume it does what it says; it seems to work; but you have no real way of telling. Using a tScheme Approved service means that you know it works. tScheme profiles are written by experts, independent of any commercial activities. They know how the magic box works. tScheme assessments are carried out by expert assessors, who also know how the magic box works. You can be assured that tScheme Approved Services are secure and work.Back to Top
- What is a Digital Signature?
Digital signatures are an electronic equivalent of the traditional signature in name only. They are, in reality, complex files of information, encoded with long algorithms, that can only be produced by the person holding the correct key. Just as only you should be able to sign your name correctly, only you, through the technology, can sign your email or other electronic communications.
Being able to rely on the quality and accuracy and, most importantly the legality, of a digital signature is part of the Electronic Communications Act 2000, which provides a framework and a legal backing to allow commerce to be done electronically. With regard to Digital Signatures, essentially the Act means that they become as legally binding as a traditional signature. As part of the Government’s wider policy to get the country online, this could eliminate the need for paper documents.
The Digital Signature is backed by a Digital Certificate, issued by a Certification Authority (CA). The role of the Certification Authority is critical. The technology to created Public and Private keys is widely available; the algorithms are openly accessible; anyone could theoretically produce their own keys.
Returning to the physical example, you need to know who has put the name above the door of the room. Who is telling you that "Bob" is "Bob Jones" in the first instance? Whilst the keys might match, guaranteeing that this message has come from a Bob Jones, how do you know it is the correct Bob Jones or that someone has not simply set up a key pretending to be Bob Jones. The name "Bob Jones" should have a certificate of its own attached. This will have been issued (and, more importantly, signed) by a Certification Authority, and whether or not you trust that authority will determine whether or not you accept Bob Jones’s identity and indeed trust the information sent.
Trusting the CA’s certificate is of course where tScheme enters the equation. tScheme produces stringent approval profiles, against which Certification Authorities’ services are independently assessed. They are assessed to very high technical, business and financial standards. Once assessed the tScheme Approvals Panel considers the Assessor’s recommendation and decides whether to approve the service and grant it the tScheme Mark. [for full details please refer to the process pages]
The Certification Authority provides the user with the Digital Certificate, which is usually produced using Public Key Cryptography (see how does the secure...). The Certificate guarantees (under terms dictated by the service provider) the identity of the user.
Back to Top
- Who can I trust to provide me with good security?
To return yet again to the analogy drawn with rooms and locks, just like at your home, you will presumably want to ensure that the lock you buy is secure. Because few people are expert locksmiths, a member of the general public may not even be able to discern the difference between two locks, let alone be able to accurately assess the security of the devices. The same issue arises with Public and Private key sets. It takes a very specialist knowledge to understand the mathematics and technology behind the keys, let alone be able to compare two or more. Therefore you need to be able to place this assessment process into the hands of people you can trust.
A provider whose service is approved by tScheme, brings with the tScheme Mark not only the confidence of a trusted name, but the knowledge that their system has been independently tested to standards drawn up by industry experts. tScheme cannot recommend a specific service over others, but you can be assured that where you see the tScheme Mark, the service has been assessed as one of the highest quality.
Back to Top